Description
Disclaimer: Copyright infringement not intended.
Context
- According to the latest report by Barracuda Networks Inc., as many as 53 per cent of organisations studied in India were victims of spear phishing in 2022.
Spear phishing definition
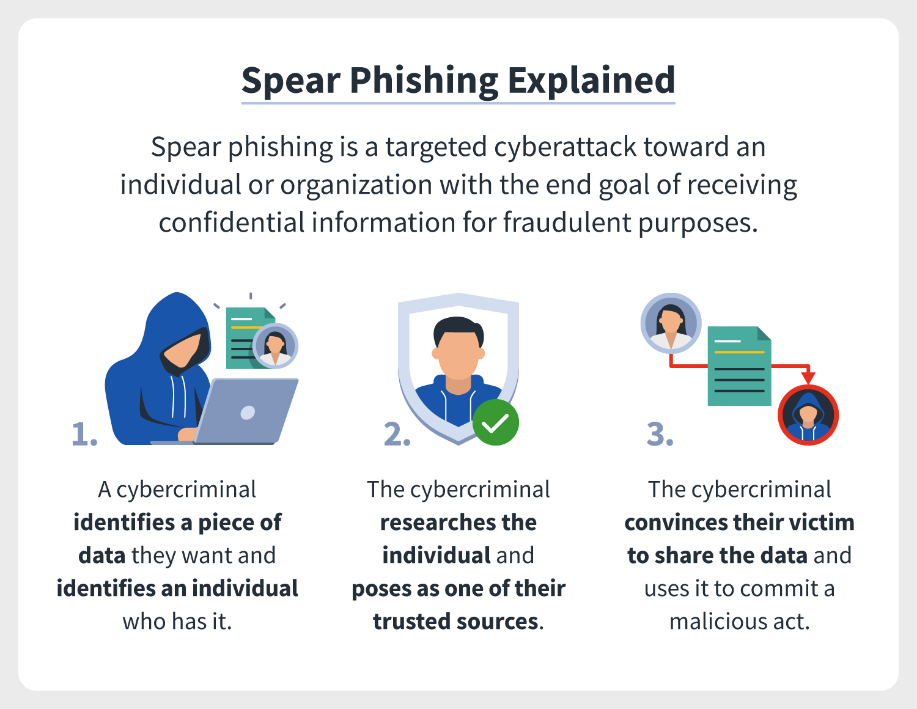
- Spear phishing is a form of phishing attack directed at specific companies or individuals.
- Cybercriminals disguise themselves as legitimate entities to extract sensitive data from their victims in the form of a phishing email or a malicious link.
- This social engineering technique is considered to be more dangerous because it can impact even tech-savvy individuals due to its personalized nature.
Spear phishing vs phishing
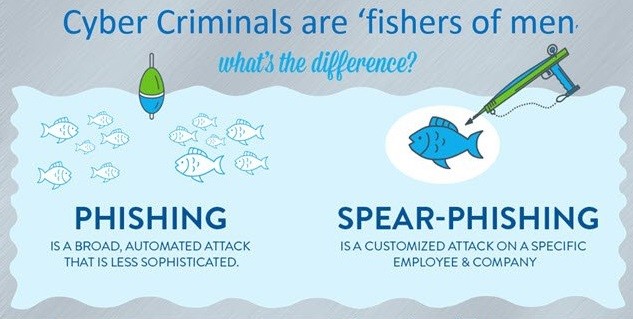
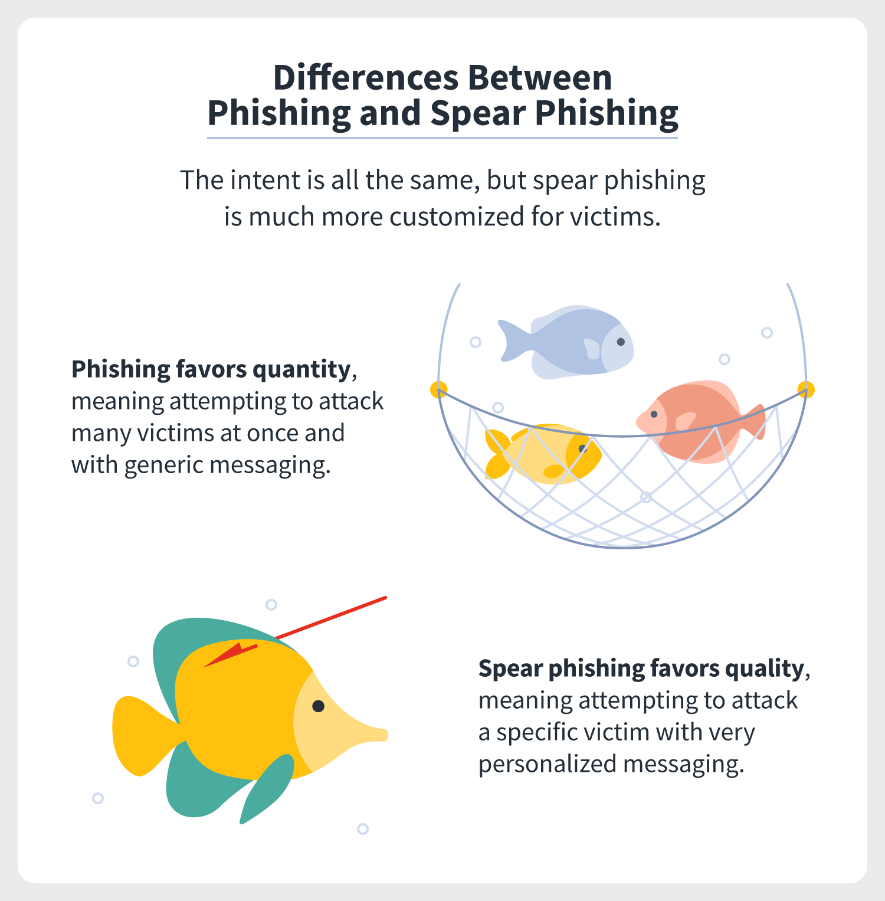
- While phishing is a random attempt at targeting as many contacts as possible, spear phishing is a focused attack on one particular target or to extract a specific piece of data.
- Spear phishing usually involves a single or a few targets, requires careful research on potential victims, and has a more specific agenda related to them. While ordinary phishing is quantitative, spear-phishing is more qualitative and focused.
Spear phishing examples
- Cybercriminals might want to target a company’s CEO to steal data or a person responsible for the organization’s security to get some important logins. Attacks targeting such senior individuals are also known as whaling.
- Cybercriminals do careful research on the organization online to find out which people to target. LinkedInis particularly useful in such cases.
- Cybercriminals personalize their messages rather than sending blasts of generic ones.
- They imitate the company’s tone of voice and communication ethics and habits to seem more genuine. They can initiate a number of false requests beforehand to find out the company’s communication patterns. For example, they might request money during the company’s payday if they know when such requests are made.
- They look through emails the company uses and create similar-looking ones via apps offering temporary email services.
MALWARE AND ITS TYPES: https://www.iasgyan.in/blogs/malwares-and-its-types
|
PRACTICE QUESTION
Q. Consider the following statements:
1. A keylogger is a surveillance malware that monitors keystroke patterns.
2. A rootkit is malicious software that enables threat actors to remotely access and control a device.
3. A bot is a self-replicating malware that spreads itself to other devices.
4. Spear phishing is a cybercrime that uses emails to carry out targeted attacks against individuals and businesses.
How many of the above statements are incorrect?
a. Only one
b. Only two
c. All four
d. None.
Answer: d. None.
|

https://www.thehindubusinessline.com/info-tech/hackers-target-indian-organisations-with-spear-phishing/article66907247.ece














