Description

Disclaimer: Copyright infringement not intended.
Context
- A draft of the cybersecurity agreement called Delhi Declaration was announced by Lieutenant-General Rajesh Pant (retd.), the National Cybersecurity Coordinator at the G20 business event held in Delhi.
About the Delhi Declaration on Cybersecurity
- It was drafted with the help of Microsoft Corporation.
- It is a series of commitments for ensuring “responsible state behaviour in cyberspace” for G-20 member countries.
- It is drawn from existing non-binding norms signed by G20 members under the auspices of the United Nations.
With the adoption of the declaration, G-20 countries would commit to the following:
- Commit not to damage critical Information infrastructure or other essential systems.
- Commit to cooperate, mitigate and investigate cyber incidents, and other malicious activities in cyberspace, in particular when it comes to ransomware.
- Commit to protect and not disrupt software supply chains.
- Commit to respect international law and the rule of law in cyberspace.
- Finally commit to protecting the humanitarian sector.
Need for agreement on Cybersecurity
- Trend towards software-isation: Vulnerabilities in cyberspace are increasing day by day as we are depending on systems that are based on hardware and software, and three is an increasing trend of software-isation.
- Cyber attacks: As the vulnerabilities grow, cyber attacks would also grow. This would cripple the critical inrasrcuitres and the Industries.
- Protection against theft and damage: Cybersecurity would protect various categories of data, including sensitive data, personally identifiable information (PII), protected health information (PHI), personal information, intellectual property, data, and governmental and industry information systems from theft and damage.
- Digital penetration: India has 52% of its population as internet users which is around 789 million people in India, as per IAMAI report. And its internet penetration is poised to increase to 900 million by 2020. This necessaries full proof Cybersecurity norms in national and international level.
- Financial data vulnerabilities: With the push for Digital India, Online National Digital Currency(ONDC), BHIM UPI etc, users of digital payment has increased manifold in recent years. As per NIC data, In FY 2021-22, 8,840 Crores Digital Payment Transactions were achieved and 20% Current & Savings Accounts were seeded with Aadhaar Number, with 81.05% Current & Savings Accounts seeded with Mobile Number. This makes it imperative to protect these users from sober threats such as phishing, ransomware, malware, etc.
- Lack of consensus on cyber law on an international level: there are a number of “existential” disagreements among countries Such as support for free flow of data by some countries and data location by others, absolute data protection versus freedom to use data, state sovereignty vs free flow of data etc. These disagreements make it difficult at international level to reach agreements.
- Cyber-Terrorism: Cyberterrorism is a term where cyberspace is used for terrorism purposes. There is a threat that national critical information infrastructure is crippled by cyber terrorism. Recent cyber attack on the Kudankulam Nuclear facility is one such example. This necessitates the need for international cooperation to fight cyber terrorism.
.jpeg)
International Agreements and initiatives
- NATO Cyber Defence Pledge: The NATO Cyber Defence Pledge, launched during NATO’s 2016 Warsaw summit, initiated cyberspace as a fourth operational domain within NATO, and emphasised cooperation through multinational projects.
- Antalya Summit Leaders’ Communiqué: The G20, in their Antalya Summit Leaders’ Communiqué, affirmed that no country should conduct or support ICT-enabled theft of intellectual property, including trade secrets or other confidential business information.
- Charlevoix commitment: The G7, in their Charlevoix commitment on defending Democracy from foreign threats, committed to “Strengthen G7 cooperation to prevent, and respond to malign interference by foreign actors which are aimed at undermining the democratic processes and the national interests of a G7 state.”
- Cybersecurity Tech Accord: The Cybersecurity Tech Accord is a commitment to foundational cybersecurity principles among global technology companies, which aims at industry responsibilities for promoting a safer online world.
- Declaration of Brazzaville: The Economic Community of Central African States (ECCAS) in 2016 adopted the Declaration of Brazzaville, which aims to harmonise national policies and regulations in the Central African subregion.
- Budapest Convention: The Council of Europe’s (CoE) Cybercrime Convention, the Budapest Convention came into force in 2004.It is supplemented by a Protocol on Xenophobia and Racism committed through computer systems. Budapest convention, are legally binding instruments.
- “Countering the use of information and communications technologies for criminal purposes” resolution”: Russia moved “Countering the use of information and communications technologies for criminal purposes” resolution in the UN and it was favoured by India. It is formulated as a counter to the Budapest convention, as the convention violates principles of state sovereignty by allowing cross-border cybercrime operations, as stated by Russia.
- Resolution 73/226 and resolution 73/27 of UNGA:
- 2015 consensus report of the UN Group of Governmental Experts (GGE) on Developments in the Field of Information and Telecommunications in the Context of International Security, proposed several norms, rules and principles for the responsible behaviour of States in cyberspace.
- The resolution 73/226 ratified the GGE consensus of the United Nations General Assembly.
- The resolution 73/27, by the Open Ended Working Group (OEWG) on developments in the field of information and telecommunications in the context of international security, was passed which is open to the entire UN membership.
- Both the UNGGE and the OEWG are supported by the UN Office for Disarmament Affairs (UNODA).
- Global Cybersecurity Agenda: The International Telecommunications Union ( ITU), a United Nations agency, launched the Global Cybersecurity Agenda, which is "a framework for international cooperation aimed at enhancing confidence and security in the information society".
- The ITU Global Cybersecurity Agenda identifies five strategic pillars: legal, technical, organizational, capacity-building, and cooperation.
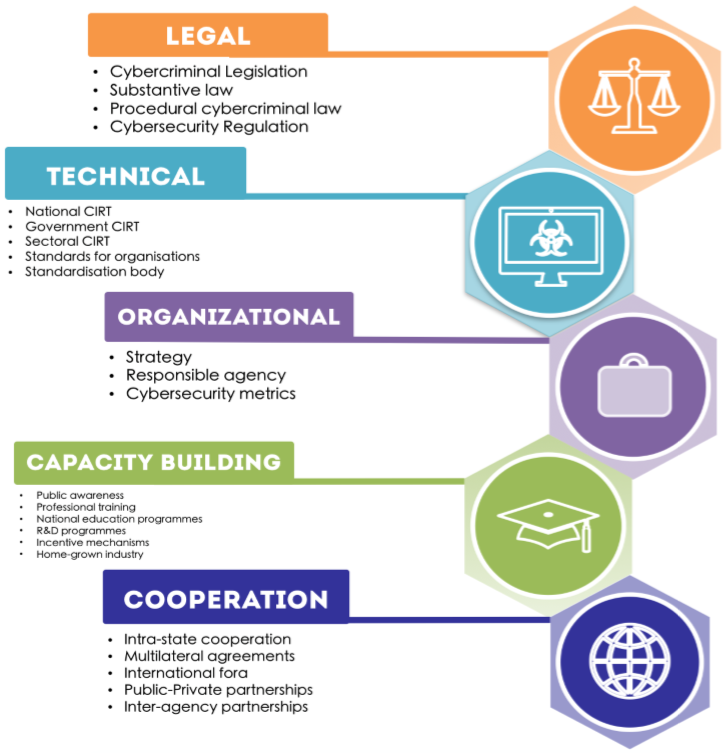
Image: Pillars of the Global Cybersecurity Index, Disclaimer: No copyright infringement is intended.
Way ahead
- Industries will have to “build resilience by building resilient cyber defence mechanisms.
- Build a competent “cyber workforce”, with the changing nature of Industries.
- establishing standard operating procedures for firms in dealing with cyber threats should be made.
- international cooperation should be done with regular vulnerability assessments and create necessary awareness of the growing cyber threat.
- Best Practice in Regulation and Mitigation of Unsolicited Communications (SPAM) and on Establishing Incident Response Teams for Internet Security (CSIRTs) should be adopted.

Conclusion
It is the need of the hour to frame a comprehensive and effective national cybersecurity strategy and international framework with respect for sovereignty of countries and with effective participation of all stakeholders. The Delhi declaration on cybersecurity is thus a step towards the right direction.
|
PRACTICE QUESTION
Q) Consider the following statement about the Budapest Convention on Cyber security:
1. It is the first international treaty seeking to address Internet and computer crime (cybercrime) by harmonising national laws.
2. It was adopted by the UN General Assembly in 2015.
3. India is a signatory of the convention.
How many of the above statements is/are correct?
- One only
- Two only
- Three only
- None
Ans: A
|
https://epaper.thehindu.com/ccidist-ws/th/th_delhi/issues/38621/OPS/G05BAOEM8.1+GV2BAP8AC.1.html
https://www.intgovforum.org/en/filedepot_download/8395/1896

















